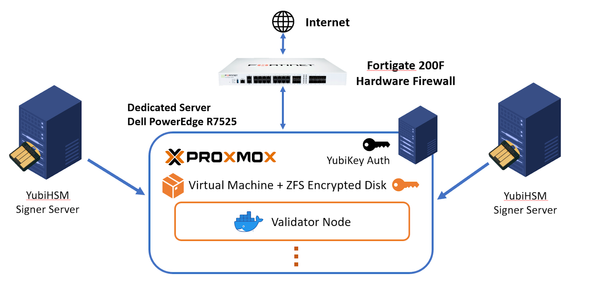
Dangerous in vanity (multiple leading zeros 0x00000…) wallets. Over $160M has been hacked!

Vanity wallets usually have many leading zeros. Many advanced users use Profanity to generate attractive wallet addresses with multiple leading zeros. Profanity has a critical security vulnerability leading to complete fund loss. These users typically have an enormous amount of tokens in their wallets. A Wintermute hacked wallet 0x0000000fe6a514a32abdcdfcc076c85243de899b is generated using Profanity which leads to the $160M Wintermute hack.
What is a vanity wallet address?
A vanity wallet address is a wallet address generated under a specific condition, such as having ten leading zeros, having ten trailing zeros, starting with 0xabc… and ending with …123.
What is the advantage of having multiple leading zeros 0x00000… vanity wallet address?
Multiple leading zeros vanity wallet address such as 0x0000000fe6a514a32abdcdfcc076c85243de899b have these advantages
- Reduce gas fees in each transaction, as explained in this blog.
- Address looks attractive
- Address looks, geek!
Why do MEV bots have many leading zeros in their addresses?
0x0000000000007F150Bd6f54c40A34d7C3d5e9f56, an active MEV bot wallet address has twelve leading zeros. Other MEV bots are following this pattern too. Usually between 10–14 leading zeros.
With an advantage in gas fee reduction, multiple leading zeros wallet addresses are widely used in the MEV industry. MEV bot developers must ultimately optimize each transaction since MEV bots perform too many frontrunning and arbitraging transactions throughout the day.
How do vanity address generation tools (Profanity and Vanity ETH) work?
Typical users can generate a vanity address using the vanity-eth tool, which provides an easy-to-use interface. It uses CPU to create a vanity address. Thus slower than using GPU. However, this tool does generate a completely random address.
More advanced users use Profanity to generate a vanity wallet address. As Profanity uses GPU to create wallet addresses, it is much faster than CPU (in a magnitude of more than 100x). However, it isn’t secure since its entropy is limited to uint32 space (2³² numbers), known as seed. This tool will then create deterministic addresses based on this seed.
This blog focuses on the security of vanity addresses, so we won’t dive deep into a walkthrough on using these tools.
How long does generating a vanity address or address with multiple leading zeros take?
i9–12900k CPU can generate 30000 addresses per second on vanity-eth. It takes a minute to generate a five leading zeros address and around ten minutes to generate six leading zeros address.
On the other hand, using hacked Profanity, T4 GPU can generate up to seven leading zeros in a matter of seconds and a minute to generate eight leading zeros. That’s approximately 300,000,000 addresses per second, vastly faster than i9–12900k CPU generation using vanity-eth. T4 is slower than the widely used RTX 3090 GPU. So, RTX 3090 should reach 500,000,000 addresses per second.
The time and cost to generate a vanity address increase exponentially as the total characters in the prefix or suffix increase.
Want to know how to generate a secure vanity address while leveraging the power of GPU? Follow our Twitter @upintern and Medium @upResearch to stay tuned.
How does the Profanity hack work?
Recall from the above section that Profanity will create deterministic addresses based on a randomized seed. That seed has an entropy of size uint32 (2³²). A hacker can brute force all seeds (2³² in total) and generate deterministic wallet addresses from each seed up to a fixed amount. To clarify, let’s give an example.
For example, if a seed 1234 uses to create addresses A, B, C, and D. Any other person who randomized seed to 1234 can recreate addresses A, B, C, and D and get private keys of these wallets.
To get the private key of wallet D, the hacker needs to know that wallet D is 4th wallet created using seed 1234. But in reality, the hacker doesn’t know the seed and order of the wallet in that seed in advance, so the hacker must brute force all seeds and brute force orders up to a fixed amount. Let’s calculate the time to brute force all seeds using 1000 T4 GPU (T4 is much slower than RTX 3090).
Assume hacker brute force up to 16,000,000 addresses on each seed (6 leading zeros). Multiply into a total of approximately 4,000,000,000 * 16,000,000 = 64,000,000,000,000,000 addresses. 1000 T4 GPU can generate 300,000,000 * 1000 = 300,000,000,000 addresses per second. In conclusion, it requires around 210,000 seconds (Approximately 60 hours) to brute force up to 16,000,000 addresses (6 leading zeros) on each seed using 1000 T4 GPU.
The journey of Profanity hack
The profanity hack journey starts when 1inch posts a warning blog titled “A vulnerability disclosed in Profanity, an Ethereum vanity address tool.” That blog highlight how the Profanity hack works and which protocols are affected. Sadly, this blog is not getting popular. So, many protocols and user wallets generated using Profanity are hacked after that.
That blog shows proof that hackers have hacked at least five deployer wallets. Luckily, the hacker can only use these wallets to claim $FORTA airdrop and dump for their profit. These wallets don’t have privilege in any governance. These protocols are 1inch, Synthetix, Autonio Foundation, Nifymoji, and Etherland. Read the tweet below from @YettyWapp for more information.
There seems to something funky going on with the $FORTA airdrop. We can assume there is a personal connection between the wallets or shared private key from the deployers claiming below and the address the tokens are transfered too...
— YettyWapp 🦇🔊 (@YettyWapp) June 16, 2022
All transactions: https://t.co/AbT02AzCWd
But not every people are lucky! A hacker successfully hacks the Wintermute governance wallet using the Profanity exploit, granted the privilege to control $160M funds in a smart contract associated with Wintermute. Librehash has written an excellent blog explaining step-by-step how Wintermute hacks work.
Although Wintermute doesn’t confirm that the hack is associated with the Profanity exploit, a security researcher has successfully replicated the hack on a simple laptop in under 48 hours by exploiting the Profanity flaw. Cryptoslate has posted the proof on their blog.
“We used a Macbook M1 with 16GB RAM to precompute a dataset in less than 10 hours… We finished the implementation and were able to crack the private key of 0x0000000fe6a514a32abdcdfcc076c85243de899b in less than 48 hours.”
Source: https://cryptoslate.com/wintermute-hack-replicated-on-simple-laptop-in-under-48-hours-by-exploiting-profanity-flaw/.
Another hack is targetting user wallets generated by the Profanity tool. PeckShield has announced that approximately 950k$ worth of crypto has been stolen by 0x9731F44b8D28e6d5c2f110f9643A3DA6c80539b9 using the Profanity exploit.
#PeckShieldAlert Seems like $950k worth of crypto has been stolen by 0x9731F from Ethereum “vanity address” generated with a tool called Profanity. The exploiter already transferred ~732 $ETH into Mixer pic.twitter.com/QOZfnE49H4
— PeckShieldAlert (@PeckShieldAlert) September 26, 2022
One wallet is losing her entire life saving in this hack, sending a message to the hacker begging to get 50% of the fund return. Everyone can find this message on-chain at this transaction.
Interesting https://t.co/ymPBoB9dR5 pic.twitter.com/lDfpEOVtfQ
— PxLinker.eth (@PxLinker_) September 26, 2022
There are other interesting cases of the Profanity hack. If you are interested, follow our Twitter @upintern and Medium @upResearch to stay tuned.
Damage of the Profanity hack
Currently, the Profanity hack is still ongoing. Analysis available publicly only covers some clusters of the hack. However, Wintermute alone is netting more than $160M in total damage. Another batch of hacks found by Peckshield caused 731 ETH (approximately 1M$). However, many cases still not yet been discovered.
Summary
Over $160M has been hacked from the Profanity hacks. Profanity hack is a tool to generate vanity addresses. It has a vulnerability in its entropy. Hackers can brute force all possible seeds of size uint32 (2³²) and scan addresses calculated deterministically using that seed up to a limited search quantity. Enormous GPU mining farms can hack all wallets with six leading zeros generated from the Profanity tool in less than three days. However, vanity-eth, a CPU alternative, doesn’t have such a vulnerability.