You shouldn’t trust everything in Etherscan: Fake transfer
Did you know that you can quickly deploy a phishing token that can impersonate anyone of your choice? We will show you how by using an example from a fake Arbitrum token.
Journey of a fake Arbitrum token
In June 2022, someone deployed a fake Arbitrum token at 0xbb3530ac51ded9c48bb74da82e803cfa334500ea by using wallet 0x7C8A99dC410e2755303f2a6DC96f1DE127E01598 as deployer. Multiple wallets have fallen into their victim.
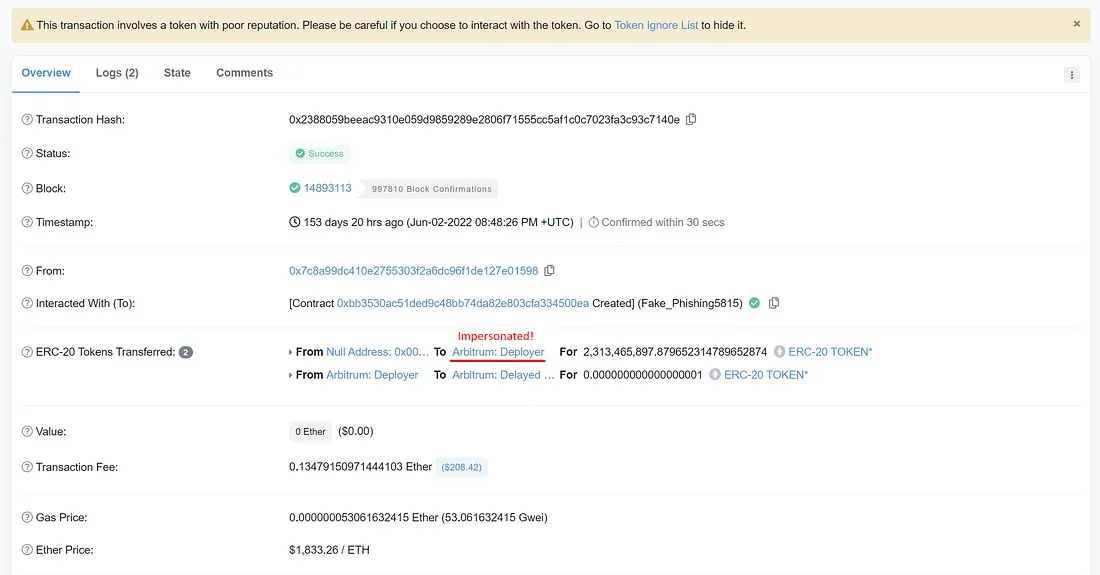
The fake Arbitrum token is recorded as having been minted to the official Arbitrum: Deployer wallet. However, tokens are minted to the phisher wallet.
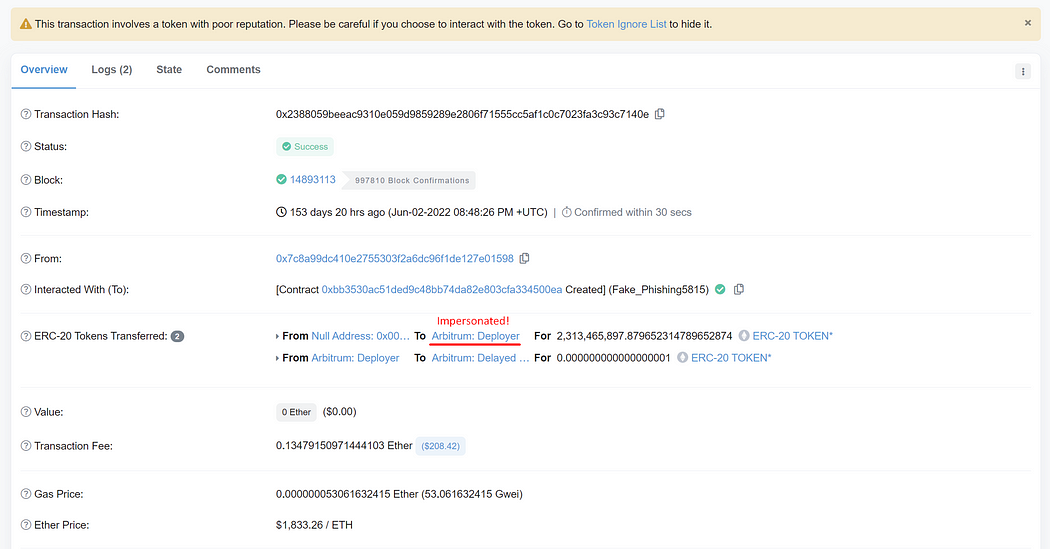
Next, the phisher impersonates the official Arbitrum: Deployer to provide liquidity to his fake token. This transaction shows that Arbitrum: Deployer pairs 45,475,808 fake tokens with 4.13 ETH. But the minted LP token is sent to the phisher wallet instead of Arbitrum: Deployer.
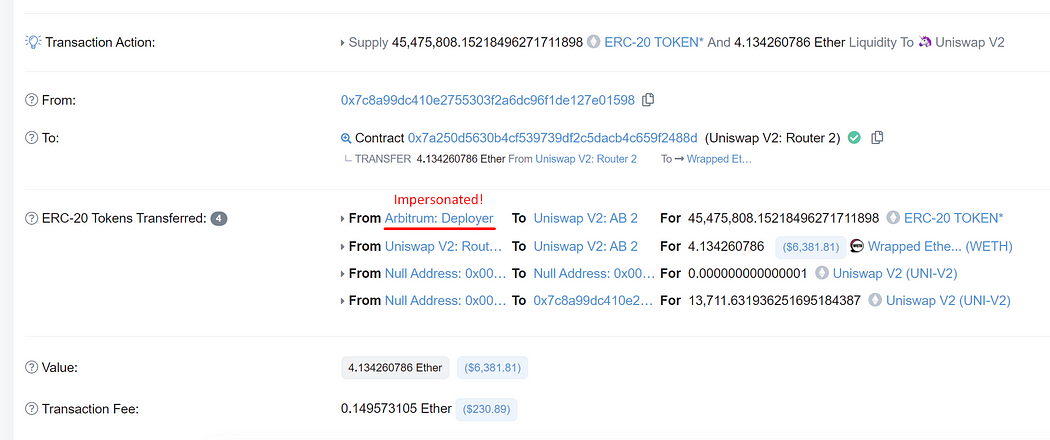
After that, the official Arbitrum: Deployer wallet distributes newly minted fake Arbitrum tokens to various official contracts. However, the official Arbitrum: Deployer isn’t responsible for these transactions since the phisher does by impersonating the official deployer.
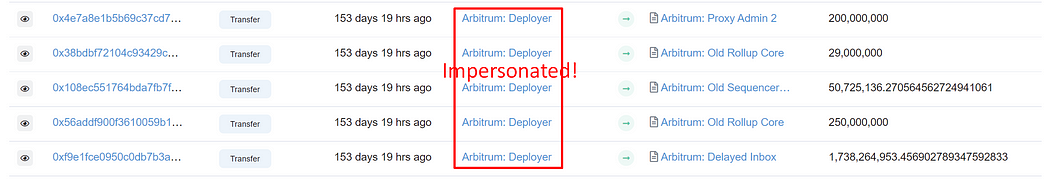
The phisher convinces others to trust his fake token by impersonating the official Arbitrum: Deployer to execute essential transactions, including liquidity provisioning and initial token distribution. The impersonation is done to have his fake token look genuine.
After that, the phisher promotes their fake Arbitrum token to multiple social networks. Moreover, the phisher also randomly pumps his fake token to create a fake volume to convince people further that it is real. Transactions are visible in his wallet in Etherscan.
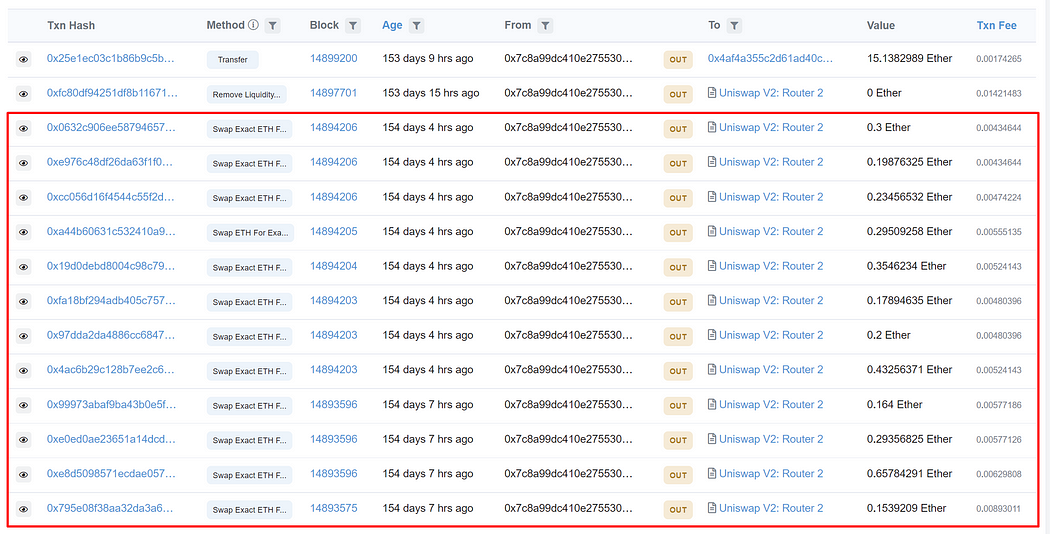
Finally, the phisher rug pulls by removing all liquidity from the fake token. 10.63 ETH is removed from the Uniswap V2 liquidity pool. The phisher received about 5 ETH in profit from this phishing.
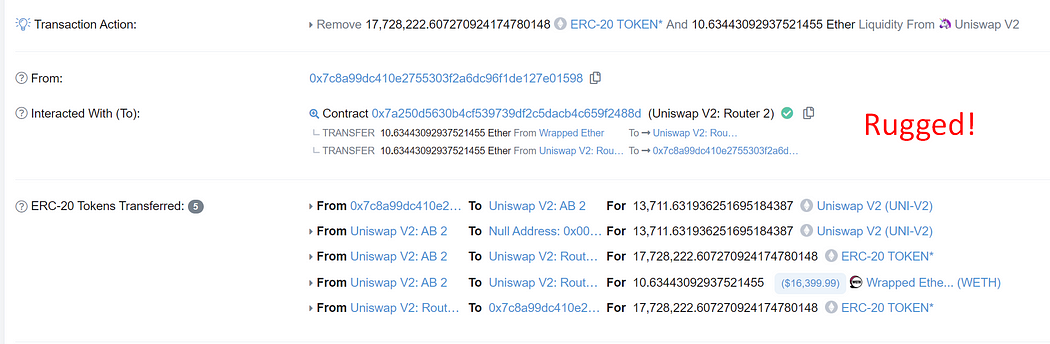
Have you ever wondered how this phisher can pass himself off as the official deployer wallet? Continue reading to find out how.
Adding arbitrary transfer records to the Etherscan
Do you know that we can deploy a custom token to add arbitrary transfer records for that token to the Etherscan? If not, we will explain how its works.
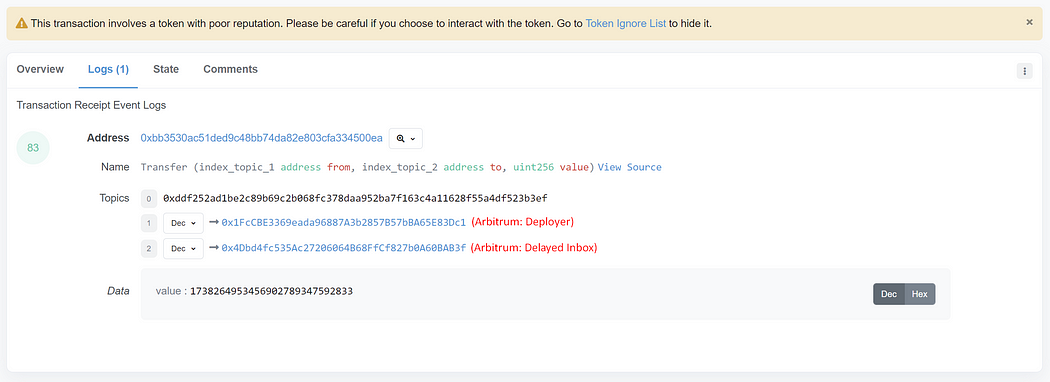
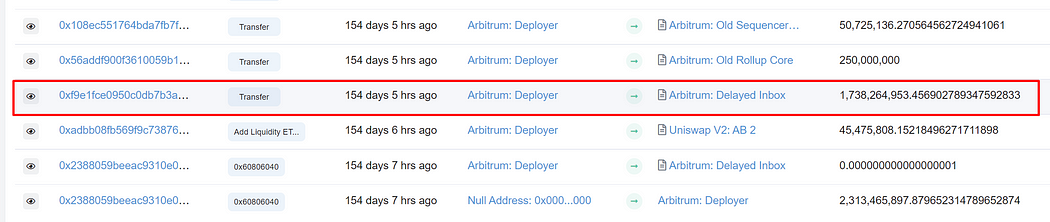
Any ERC-20 compatible smart contract that emits a “Transfer” event creates a transfer record in Etherscan for each “Transfer” event emitted. Smart contracts that are ERC-20 compliant need to have the same set of functions and input and output specifications. However, it doesn’t check whether each function’s implementation adheres to the specification. Therefore, anybody can change the implementation to carry out unexpectedly bad actions, including creating arbitrary transfer records without transferring anything.
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.0;
import "@openzeppelin/contracts/token/ERC20/ERC20.sol";
contract FakeERC20 is ERC20("Just for test", "FAKE") {
function transferFrom(address from, address to, uint256 amount) public virtual override returns(bool) {
emit Transfer(from, to, amount);
return true;
}
} We have developed an example contract to demonstrate the maliciously adding arbitrary transfer records to the Etherscan. We have shared its source code above.
This contract has been deployed at 0x7467bff531c07FAB10E94f3495bD493A4cFa2114 on the Goerli testnet. Feel free to test this contract by executing the transferFrom function with arbitrary from, to, and amount parameters. Notice that a new ERC20 transfer record is added to the victim’s wallet without the victim’s permission.
The transferFrom function is overridden only to emit the “Transfer” event. When the “Transfer” event is emitted, it is automatically included in the Etherscan without additional confirmation. Typically, it must check allowance permission and update the balance before emitting the “Transfer” event.
Impersonating Vitalik’s wallet
We can impersonate Vitalik’s wallet as the token sender by passing Vitalik’s wallet (0xAb5801a7D398351b8bE11C439e05C5B3259aeC9B) to the “from” parameter of the “transferFrom” function on our fake token contract. You can freely set other parameters to your own choice. In this example, we will set our deployer as “to” and 1,000,000 ethers as “amount.”
Navigate to the write contract page on our fake token on Goerli’s Etherscan, switch to Goerli testnet, connect your wallet, and execute the “transferFrom” function with the above parameters.
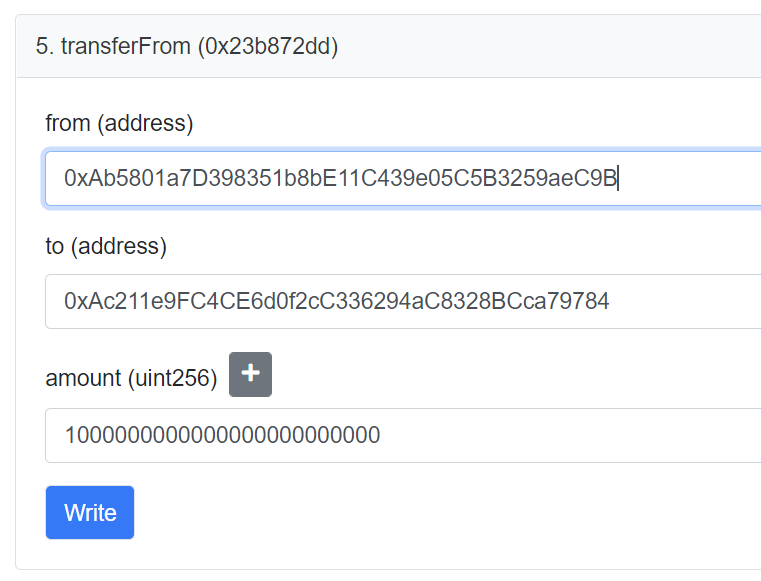
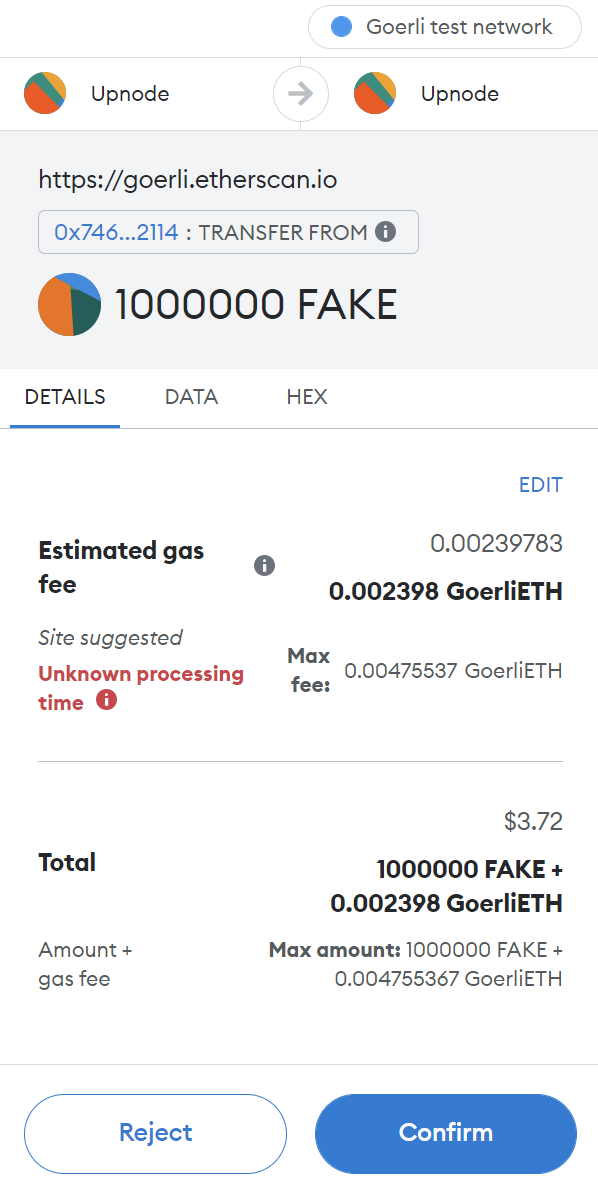
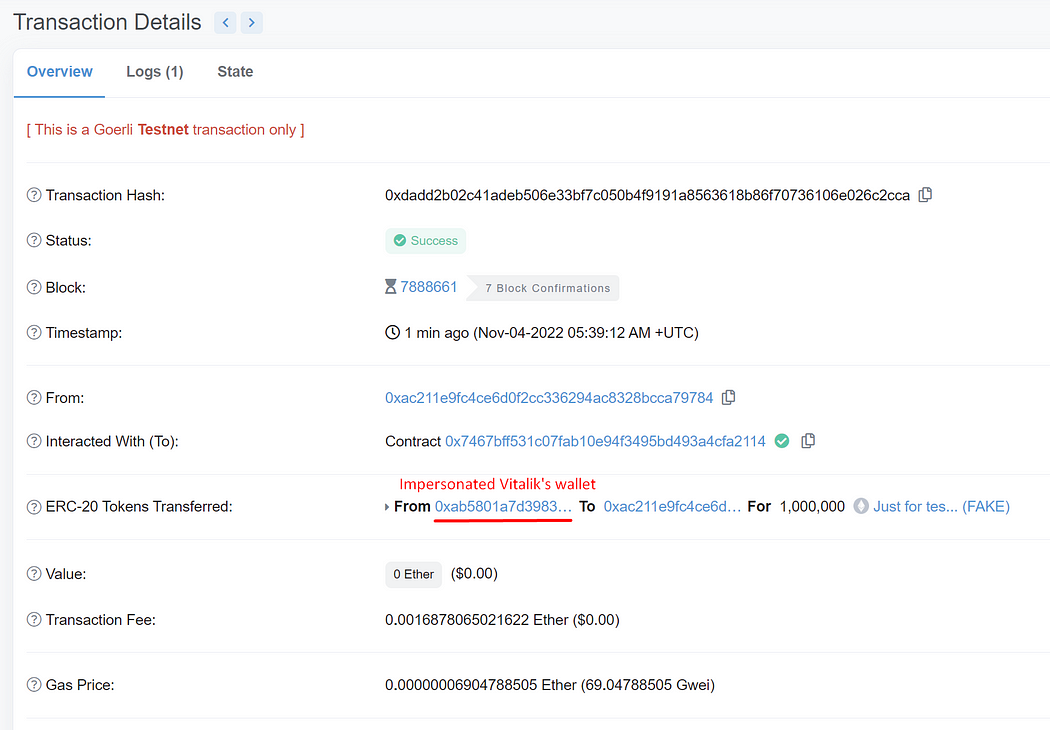
After “transferFrom” has been executed, head over to the ERC20 Token Txns of Vitalik’s wallet. Observe that a transfer of our fake token totaling 1,000,000 from Vitalik’s wallet to our deployer wallet has been noted in this transaction. However, if you check our deployer wallet’s balance, we still have no tokens. The transfer isn’t actually performed. As a result, we have successfully impersonated Vitalik’s wallet.
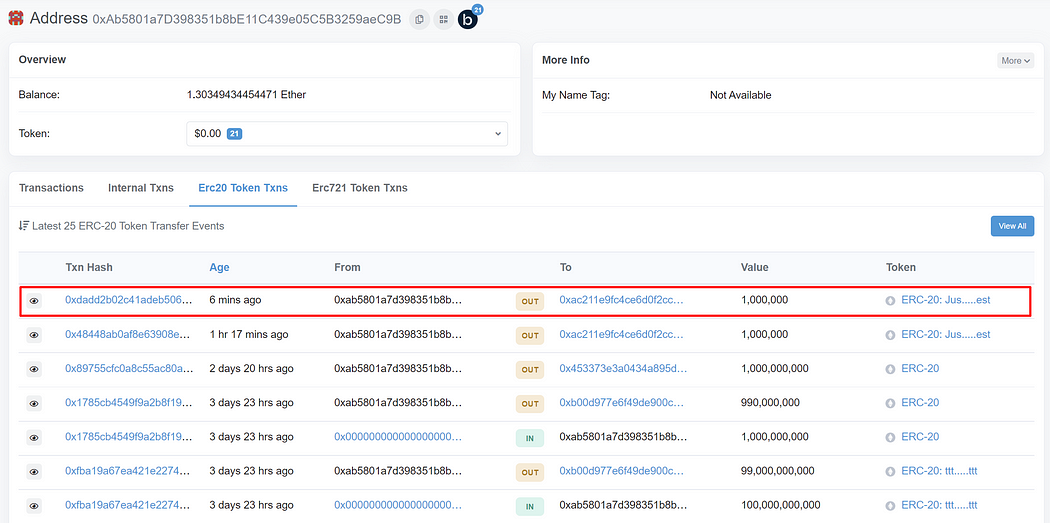
Technical concepts in the fake Arbitrum token
In this contract, there are two essential parts: The _transfer and _mint functions. All impersonations are done using the modification to these two functions.
The _transfer function
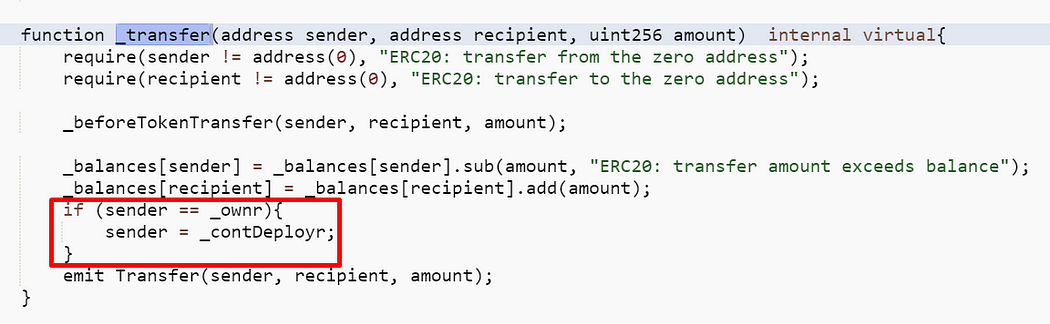
The _transfer function is modified to set the sender to the official Arbitrum deployer wallet before emitting the “Transfer” event if the phisher (_ownr) sends his token. Other parts remain as usual.
As a result, for every token transfer from the phisher wallet, the token balance got deducted from the phisher wallet as usual. However, Etherscan will show that the token is sent from the official Arbitrum deployer wallet.
The _mint function
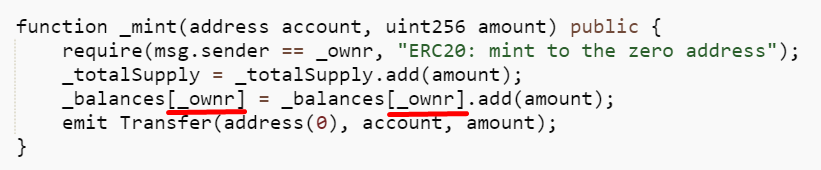
The _mint function is modified to only mint tokens to the phisher wallet (_ownr) while emitting a modified “Transfer” event that changes the token receiver to anyone of his choice. In this case, the phisher modifies the “Transfer” event to record token minting to the official Arbitrum deployer wallet.
The procedure of fake Arbitrum token phishing
- Deploy a fake Arbitrum token contract. View the transaction here.
- Mint token to the phisher wallet, but impersonate that official Arbitrum deployer minted the token using _mint function. View the transaction here.
- Provide liquidity using a standard Uniswap V2 interface. Modifying the _transfer function will update the liquidity provider recorded in Etherscan to the official Arbitrum deployer wallet (*). View the transaction here.
- Transfer tokens to multiple official contracts using a standard wallet. Modifying the _transfer function will record in Etherscan that the official Arbitrum deployer wallet is airdropping tokens to these contracts (*). View logs on the token page.
- The phisher promotes his fake token on his social media.
- The phisher randomly pumps his fake token. People are rushing to buy the token in FOMO. View logs on the phisher wallet page.
- The phisher commits a rug pull by removing all liquidity, taking home approximately 5 ETH in profit. View the transaction here.
- Profit is transferred to his new wallet to get ready for the next phishing. View the transaction here.
(*) Any token sent from the phisher wallet will be recorded as the official Arbitrum deployer wallet.
Summary
Transfer logs of questionable tokens on Etherscan cannot be trusted. By employing arbitrary “Transfer” logs emitting alteration, it is made to look real. However, it isn’t. The recorded sender is being impersonated. Impersonated senders aren’t responsible for any of these transactions. An important example is the fake Arbitrum token, where the official Arbitrum deployer is impersonated to provision initial liquidity and distribute tokens to multiple official contracts. The impersonation is done to have his fake token look genuine.
This phisher is a serial scammer. If you trace the transaction deeply, you will notice that this phisher conducts this kind of phishing multiple times. Profiting more than 40 ETH. Follow us on Medium and Twitter to stay tuned.